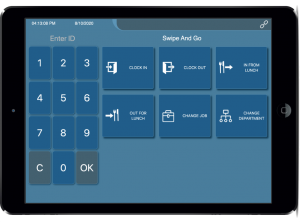
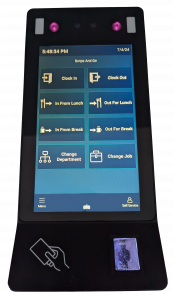
Choose Your Web Package
Provides the essential labor management tools
See All Features Hide Details- Real-Time Interactive Dashboard & Status Board
- Employee Login, Web & Mobile Access
- Popular Payroll Exports & Payroll Wizard
- Geo-Fencing & GPS Location on Mobile
- Employee Badge & Template Repository
- Popular Reports
- Employee Job Transfer
- Real-Time Device Transactions
- Late lunch, short lunch, no lunch feature
- Multiple Organization Levels
- Shift Assignment & Management
- GPS Tracking on Mobile
- Job/Department Transfer & Costing
- Seamless Payroll Integrations & 120+ Exports
- Report Designer /w 60+ Customizable Reports
- ACA Compliance
- Advanced Rounding
- Notifications via Email and Mobile
- USigned Digital Signature
- Benefit Accrual & Mandatory Sick Pay
- Banked Hours for Future PTO
- Canadian Statutory Holidays
- SQL Read-Only Access
Provides solutions for more complex labor management needs
See All Features Hide Details- Real-Time Interactive Dashboard & Status Board
- Employee Login, Web & Mobile Access
- Popular Payroll Exports & Payroll Wizard
- Geo-Fencing & GPS Location on Mobile
- Employee Badge & Template Repository
- Popular Reports
- Employee Job Transfer
- Real-Time Device Transactions
- Late lunch, short lunch, no lunch feature
- Multiple Organization Levels
- Shift Assignment & Management
- GPS Tracking on Mobile
- Job/Department Transfer & Costing
- Seamless Payroll Integrations & 120+ Exports
- Report Designer /w 60+ Customizable Reports
- ACA Compliance
- Advanced Rounding
- Notifications via Email and Mobile
- USigned Digital Signature
- Benefit Accrual & Mandatory Sick Pay
- Banked Hours for Future PTO
- Canadian Statutory Holidays
- SQL Read-Only Access
Provides all advanced features plus specialized solutions
See All Features Hide Details- Real-Time Interactive Dashboard & Status Board
- Employee Login, Web & Mobile Access
- Popular Payroll Exports & Payroll Wizard
- Geo-Fencing & GPS Location on Mobile
- Employee Badge & Template Repository
- Popular Reports
- Employee Job Transfer
- Real-Time Device Transactions
- Late lunch, short lunch, no lunch feature
- Multiple Organization Levels
- Shift Assignment & Management
- GPS Tracking on Mobile
- Job/Department Transfer & Costing
- Seamless Payroll Integrations & 120+ Exports
- Report Designer /w 60+ Customizable Reports
- ACA Compliance
- Advanced Rounding
- Notifications via Email and Mobile
- USigned Digital Signature
- Benefit Accrual & Mandatory Sick Pay
- Banked Hours for Future PTO
- Canadian Statutory Holidays
- SQL Read-Only Access